When you think about protecting yourself from hackers, what do you imagine? A nerdy genius clacking away at a keyboard as he writes computer code to steal your data? In reality, it’s nothing like the movies; far and away the most common type of hacking is phishing, which barely requires any tech smarts at all.
Phishing is a form of social engineering designed to simply trick you into giving your data away freely. There’s no need for complicated hacking if a scammer can just ask for your password. Of course, most scams are more involved than that, and these days there’s some remarkably convincing fake messaging going on. Mistake a phony email or text message for the real deal, and before long you could have inadvertently given a small fortune away.
So how can you protect yourself from these phishing attacks? Firewalls and content blockers can’t do much against this kind of trickery, but a little learning can make all the difference. Familiarize yourself with these classic scamming staples and you’ll be better prepared to identify a hoax when you see one.
Phony calls
We’ve all heard the robo-diallers with their irritating pre-recorded trickery. But on iOS, callers can sometimes spoof their identity to make an incoming call look legit.
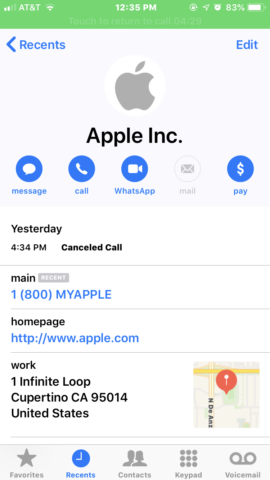
Example: This scam involves an automated call that purports to come from Apple. The call claims that Apple’s servers have been compromised and the user’s Apple ID account is at risk. The solution, of course, is to call the scammers back on a given number and divulge your login details. A classic phishing attack.
What makes this a particularly potent scam is that the call shows up in the Phone app as if it had genuinely come from Apple. The contact image, name, address, and support number all correspond to Apple’s real details. This makes for a pretty convincing impression that the call is legitimate. Surprisingly, even genuine calls from Apple’s real support team get lumped in with this fake correspondence in your call history.
Fake iOS alerts
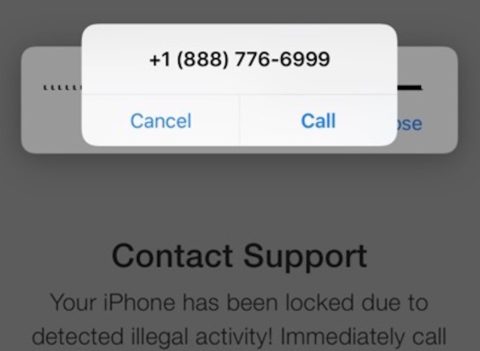
Sometimes a phone scam will go further, starting with a legit-looking pop-up in iOS that prompts you to call a number. Here’s one we found doing the rounds.
Example: Firstly, a batch of fake emails is targeted at known iCloud users. The email contains a “critical alert” warning and a link to a fake (but fairly convincing) Apple website that says your device has been “locked for illegal activity.” This website then launches a pop-up that looks just like the iOS system alert, prompting the user to call AppleCare immediately to fix the problem.
Unsuspecting users who follow these instructions get through to a fake support team based in India whose only job is to mine you for personal information like your usernames and passwords. Don’t be fooled.
Cancellation emails
Emails claiming to be from an authority can be pretty convincing, especially when confirmation of a (totally non-existent) large payment sum causes logic to jump out the window. This type of email could be themed around anything – bank accounts, gym memberships, you name it – but the example we found below is specific to App Store subscriptions.
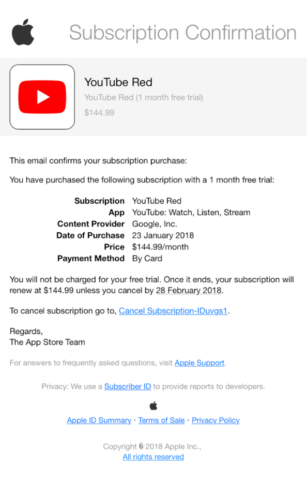
Example: A fraudster will mock up an email showing a real-looking subscription confirmation from Apple. It usually shows a free trial for a real product, that will – apparently – roll onto a full subscription at an exorbitant price, often hundreds of dollars per month. Of course, none of this is true and prices like $145/month for YouTube (as seen below) should be a clear sign that somebody is taking you for a ride. But that’s one convincing-looking email!
These emails attempt to shock users into hitting the “unsubscribe” button without giving it a second thought. The button then takes them to an authentic-looking page where they’re asked to input personal details such as Apple ID logins and even credit card details in order to cancel the subscription. Which, lest we forget, doesn’t exist in the first place.
How to identify a hoax
So with those three examples in mind, you should have a good idea of what to look for. But there are a few more rules of thumb when it comes to sniffing out a hoax.
Essentially, you’re turning detective in the hunt for details that don’t look right. Check whether the sender’s contact details match the company it claims to be from. Likewise, check the URL of any links before clicking them to see if the address looks legit. For example, an email from Apple should come from an @apple.com email address, and any links should go to an address including the domain apple.com.
Unsolicited messages should always be viewed with caution, especially if they request personal information. Very few companies will ask for sensitive data by text. If you receive a message or email with an attachment, don’t open it until you’re happy you trust the sender.
Stay cool
Most of these scams use urgency (“If you don’t respond within 24 hours you’ll be charged $1000!”) to encourage people to let their guard down.
If something seems off, don’t rush into anything, and definitely don’t use the links or phone numbers provided in any messaging that feels suspect. Instead, independently research the source company’s website and use the contact details provided to check everything’s ok.
You can always speak to Apple’s security support team if you’re concerned about a security risk on your device – and suspicious emails can be forwarded to reportphishing@apple.com to help them tackle the scammers directly.
Finally, remember there are plenty more scams out there than the few we covered here – and they get more sophisticated by the day. Be smart. Stay cool. Think twice.